Apr 24, 2017 I have business in a box on my computer and I have tried to uninstall it and I keep getting a message.1 This publisher has been blocked from running software on your machine. Name: c: Program Files (x86) Business-in-a-Box installer.exe. Publisher: ut.PointerPoint. Type: Application. From: C: Program Files (x86) Business in a Box Installer.exe.
Scalable, comprehensive endpoint security against malware, viruses, ransomware, exploits, and other zero-day threats designed to keep your business running smoothly.
Looking to protect your personal devices?Learn more
- Feb 12, 2020 business-in-a-box.exe is certainly a possibly unwanted app that may be currently running in your device. By the way, business-in-a-box.exe will certainly appear in Task Manager of your computer. This process is not malware in the complete definition of this word, nevertheless, its existence in your gadget is the sign of a significant problem.
- Source: Business-i n-a-BoxSe tup.exe, 0 0000002.15.0 000000005A 0004.00000 001.sdmp, Business-i n-a-BoxSe tup.exe, 0 0000002.17.0 000000000E 0004.00000 001.sdmp, Business-i n-a-BoxSe tup.exe, 0 0000002.18.0 000000000E 0004.00000 020.sdmp, CF927E5B.
Malwarebytes Endpoint Protection
Cloud management console for full security control
Buy NowContact UsMalwarebytes for Teams
Stand alone solution for small business and home offices
Buy NowEnterprise-grade platform, small business simplicity
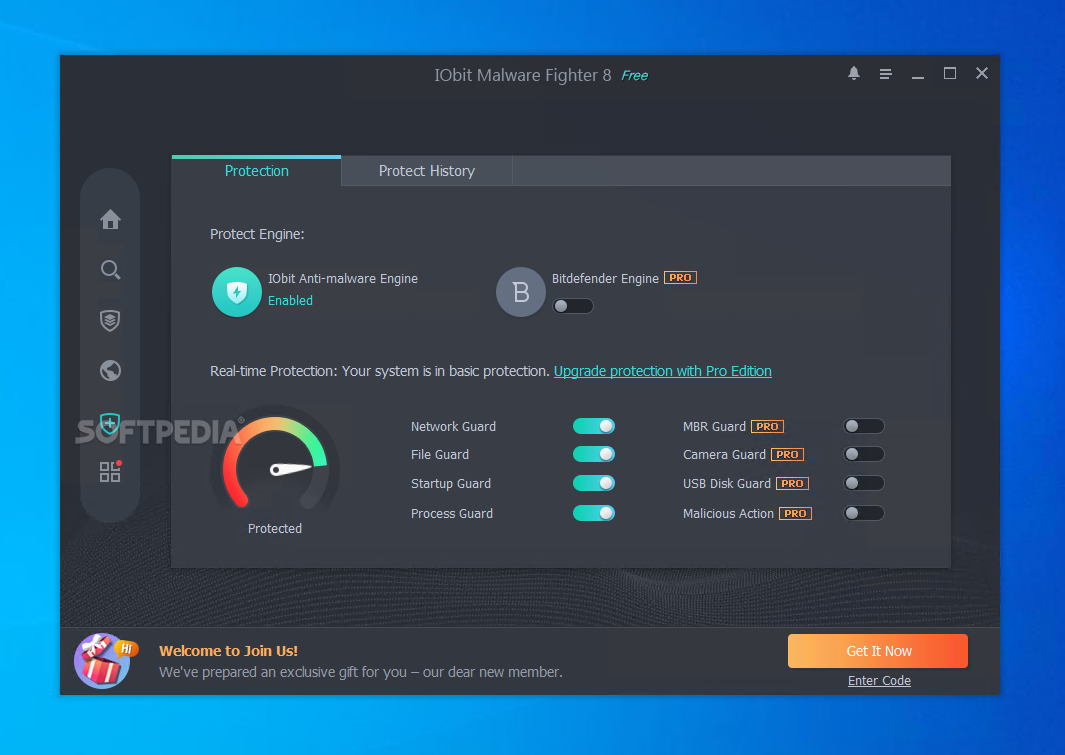
Our cybersecurity solutions offer unmatched threat protection, detection, and response capabilities that can grow with your business. You can use Malwarebytes as a standalone endpoint security solution for your small office or as a centrally managed cybersecurity platform to meet your growing business needs. There's a reason why Malwarebytes is trusted by businesses worldwide as the go-to solution for remediation, removing more than a million threats each day.
30-day Free TrialLearn More
Complete and thorough remediation
Our solutions contain the threat by isolating the infected endpoint, followed by comprehensive removal of the threats and all associated artifacts. Ransomware rollback restores the endpoint to the last known good state.
Enterprise grade protection
Our business solutions bring a multi-layer defense model that combines advanced malware detection, malicious website blocking, ransomware blocking, and exploit protection in a single integrated solution that scales with your business needs.
Unmatched threat visibility
With more than four million threats detected or blocked every day, Malwarebytes has unprecedented visibility into cyberthreats and attacks. This unique real-time insight enables us to fully understand the attacks and better anticipate future threats.
Centralized management
The Malwarebytes management console provides centralized policy management and consolidated threat visibility across all your business endpoints. This significantly reduces costs and efforts to securely maintain and manage our endpoints.
See what we have to offer
Case studies
Malwarebytes for Home
We also offer comprehensive cybersecurity for your personal devices.

How Does Antivirus Software Work?
Any time you open or download a new file, an antivirus program will scan the files for viruses and other harmful executables. Almost every free anti virus software today features multiple scanning detection processes. The most basic detection process is called 'specific detection.' It works by scanning a file for various sets of characteristics and checking these characteristics against a list of already known malware. This process is an essential component of an antivirus software, and essential for every free PC antivirus, but it is also easy for cybercriminals to evade. All a cybercriminal must do is modify the malware code slightly to render it undetectable.

The top free antivirus, Comodo Antivirus, does not rely only on specific detection. Comodo also uses heuristic detection and containment to ensure that even unknown malware cannot compromise our users' computers. Heuristic detection is a method of analyzing a file to determine if it contains suspicious code. If suspicious code is detected then the antivirus deletes the file or recommends it for containment. Files run in Comodo containment are kept in a sandbox environment, separate from your operating system. Heuristics is about detecting virus-like behavior or attributes rather than looking for a precise virus signature that matches a signature on the virus blacklist.
A common misconception that lingers to this day is that free antivirus protection is not adequate to deal with malware threats. Though this pay have been true in the past, today's best free antivirus software have features that can keep you protected from even the most advanced malware. The best free antivirus on the market today, Comodo Antivirus offers features more advanced than most paid antiviruses. Comodo Antivirus gives users a major advantage over not only an antivirus-free environment, but also the best paid antivirus products on the market.
Best Virus Protection Software from Comodo
Comodo's virus protection technology has proved its mettle for battling virus threats through tried-and-tested methods. Infection Defense+ barricades the access of any dubious programs at all critical checkpoints, while the Auto-Sandbox Techniques isolates the potentially harmful programs in a restricted environment without letting it affect your workflow.
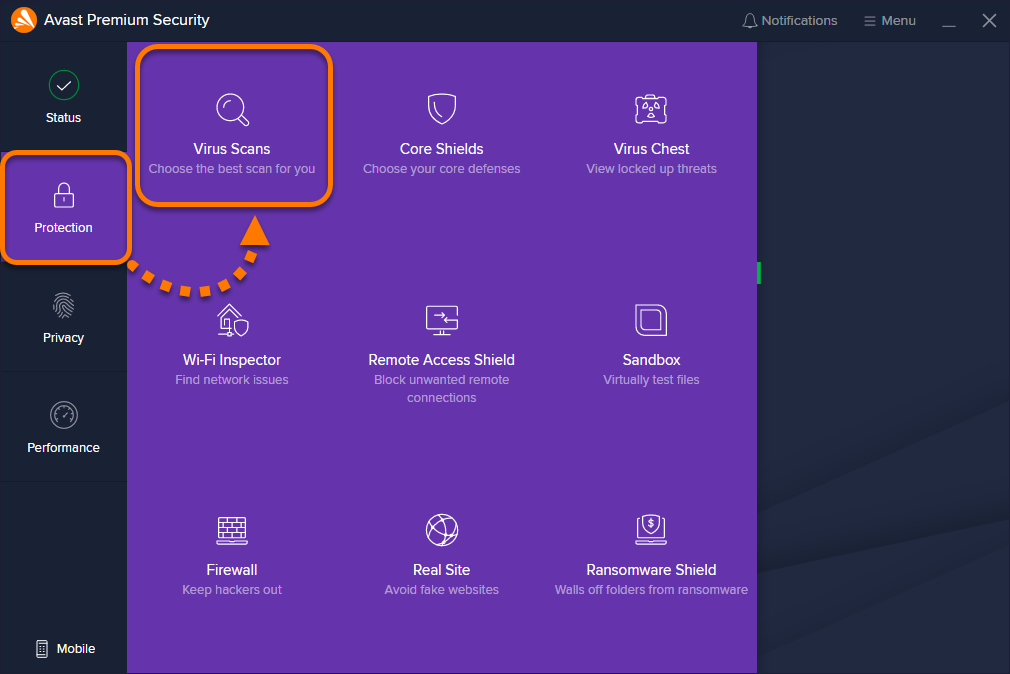
Our cybersecurity solutions offer unmatched threat protection, detection, and response capabilities that can grow with your business. You can use Malwarebytes as a standalone endpoint security solution for your small office or as a centrally managed cybersecurity platform to meet your growing business needs. There's a reason why Malwarebytes is trusted by businesses worldwide as the go-to solution for remediation, removing more than a million threats each day.
30-day Free TrialLearn More
Complete and thorough remediation
Our solutions contain the threat by isolating the infected endpoint, followed by comprehensive removal of the threats and all associated artifacts. Ransomware rollback restores the endpoint to the last known good state.
Enterprise grade protection
Our business solutions bring a multi-layer defense model that combines advanced malware detection, malicious website blocking, ransomware blocking, and exploit protection in a single integrated solution that scales with your business needs.
Unmatched threat visibility
With more than four million threats detected or blocked every day, Malwarebytes has unprecedented visibility into cyberthreats and attacks. This unique real-time insight enables us to fully understand the attacks and better anticipate future threats.
Centralized management
The Malwarebytes management console provides centralized policy management and consolidated threat visibility across all your business endpoints. This significantly reduces costs and efforts to securely maintain and manage our endpoints.
See what we have to offer
Case studies
Malwarebytes for Home
We also offer comprehensive cybersecurity for your personal devices.
LEARN MOREHow Does Antivirus Software Work?
Any time you open or download a new file, an antivirus program will scan the files for viruses and other harmful executables. Almost every free anti virus software today features multiple scanning detection processes. The most basic detection process is called 'specific detection.' It works by scanning a file for various sets of characteristics and checking these characteristics against a list of already known malware. This process is an essential component of an antivirus software, and essential for every free PC antivirus, but it is also easy for cybercriminals to evade. All a cybercriminal must do is modify the malware code slightly to render it undetectable.
The top free antivirus, Comodo Antivirus, does not rely only on specific detection. Comodo also uses heuristic detection and containment to ensure that even unknown malware cannot compromise our users' computers. Heuristic detection is a method of analyzing a file to determine if it contains suspicious code. If suspicious code is detected then the antivirus deletes the file or recommends it for containment. Files run in Comodo containment are kept in a sandbox environment, separate from your operating system. Heuristics is about detecting virus-like behavior or attributes rather than looking for a precise virus signature that matches a signature on the virus blacklist.
A common misconception that lingers to this day is that free antivirus protection is not adequate to deal with malware threats. Though this pay have been true in the past, today's best free antivirus software have features that can keep you protected from even the most advanced malware. The best free antivirus on the market today, Comodo Antivirus offers features more advanced than most paid antiviruses. Comodo Antivirus gives users a major advantage over not only an antivirus-free environment, but also the best paid antivirus products on the market.
Best Virus Protection Software from Comodo
Comodo's virus protection technology has proved its mettle for battling virus threats through tried-and-tested methods. Infection Defense+ barricades the access of any dubious programs at all critical checkpoints, while the Auto-Sandbox Techniques isolates the potentially harmful programs in a restricted environment without letting it affect your workflow.
Test Malware Exe
Lightroom classic 10. Comodo antivirus 2021 also features the Default Deny Protection which, as opposed to other security software, denies access to a program if it's not in Comodo's comprehensive whitelist. The cloud-aware security features are light on the system and provide constant virus scanning and behavior analysis report.

